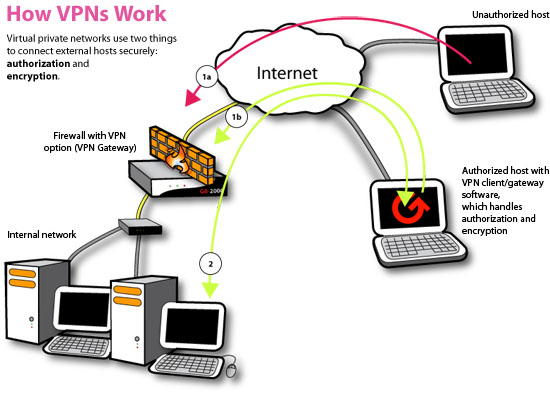
VPN (Virtual private network) is a secure connection between two or more endpoints. It can also be seen as an extension to a private network.
A VPN is commonly used to provide secure connectivity to a site. There are two key types of VPN scenarios, Site to Site VPN and a Remote Access VPN.
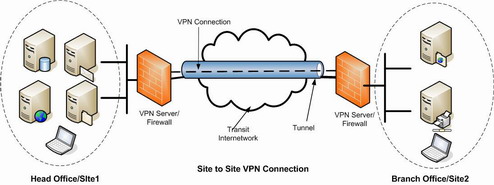
Site to Site VPN
In a site to site VPN, data is encrypted from one VPN gateway to the other, providing a secure link between two sites. This would enable both sites to share resources over the VPN link.
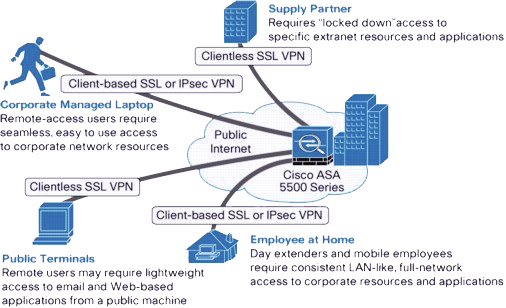
Remote Access VPN
In a remote access VPN a secure connection would be made from an individual computer to a VPN gateway. This would enable a user to access their e-mail, files and other resources at work from where ever they may be, providing they have an internet connection. There are two common forms of technlogy that exists in remote access or mobile VPN known as IPSec and SSL.
Why have a VPN
A VPN saves companies from renting a dedicated leased line, also enables users to work from home, and saves cost on resources such as e-mail servers, file servers, etc, as all these can be accessed on the VPN connection at the central site.
A real world example would be if a company was split into two sites, the main site in the US and a smaller site in the UK. The US site had already a full network infrastructure in place which consisted of active directory, an exchange server, file server and so on. The UK site only consisted of a small number of users, letís say 10 employees. To make this particular scenario cost effective a VPN connection from site to site would be the best way. Providing a VPN tunnel from the UK site to the US site would save costs from having to install another exchange server, active directory server and so on. As the US site would already have administrators maintaining servers and the infrastructure and can now maintain the VPN connection as well as other resources would prove another area where savings would be made. A remote access VPN scenario would be suited if the 10 users were not based anywhere in particular, and there was no UK based office. In this case they would just require an internet connection and a configured VPN client software enabling them to securely connect to their corporate network in the US. If they were using SSL VPN then they would not even require a configured client side software, they would just require the URL address to connect to the VPN portal.
So VPNís provide a superb and cost effective solution for companies with several branch offices, partners, and remote users to share data and connect to their corporate network in a secure and private manner.
With normal internet traffic, packets can be sniffed and read by anyone. However sending data via a VPN tunnel encapsulates all data packets providing high level of security. If packets which were sent securely over the internet were sniffed, they would be unreadable and if modified this would also be detected by the VPN gateway.
VPN Networking Protocols
VPN tunnels use one of four main networking protocols, which provide the sufficient level of security as shown below;
PPTP (Point to Point tunneling protocol)
PPTP is a protocol or technology that supports the use of VPNís. Using PPTP, remote users can access their corporate networks securely, using the Microsoft Windows Platforms and other PPP (Point to Point tunneling Protocols) enabled systems. This is achieved with remote users dialling into their local internet security providers, to connect securely to their networks via the internet.
PPTP has its issues and is considered as a weak security protocol according to many experts, although Microsoft continues to improve the use of PPTP, and claims issues within PPTP have now been corrected. Although PPTP is easier to use and configure than IPSec, IPSec outweighs PPTP in other areas such as being more secure and a robust protocol.
L2TP (Layer 2 Tunneling Protocol)
L2TP is an extension of the PPTP (Point to point tunneling protocol), used by internet service providers to provide VPN services over the internet. L2TP combines the functionality of PPTP and L2F (Layer 2 forwarding protocol) with some additional functions using some of the IPSec functionality. Also L2TP can be used in conjunction with IPSec to provide encryption, authentication and integrity. IPSec is the way forward and is considered better than the layer 2 VPNís such as PPTP and L2TP.
IPSec (IP Security)
IPSec operates on layer 3 and so can protect any protocol that runs on top of IP. IPSec is a framework, consisting of various protocols and algorithms which can be added to and developed. IPSec provides flexibility and strength in depth, and is an almost perfect solution for securing VPNís. The only drawback is IPSec requires setting up on the corporate network and on the client end and is a complex framework to work with.
SSL VPN (Secure Socket Layer)
SSL VPN provides excellent security for remote access users as well as ease of use. SSL is already heavily used such as when you shop online, accessing your bank account online, you will notice an SSL protected page when you see the ďhttpsĒ in your browser URL bar as opposed to ďhttpĒ. The difference in using SSL VPN to IPSec is with IPSec a remote user would require client software which would need to installing, configuring and sometimes troubleshooting. However with SSL client software, it can be installed with very little effort via a browser, which simplifies the process in securely accessing the corporate network.
Using SSL VPN would mean thousands of end userís would be able to access the corporate network without the support of an administrator, and possible hours of configuring and trouble shooting, unlike IPSec. The end user would just need to know the address of the SSL VPN portal. Another advantage is they can do this from any computer as they do not have to rely on a configured client side software.
Advantages and Disadvantages using a VPN
Advantages
VPNís eliminate the need for expensive leased lines. Historically T1 lines have been used connecting office locations together in a secure manner. If the office locations are further away, the cost of renting these least lines can be unbearable. A VPN though, only requires you to have a broadband internet connection, and so avoiding paying a hefty sum of monthly rental on dedicated leased lines. VPNís are also a replacement for remote access serverís and dial up network connections although rarely used anymore.
Having many branch offices over the globe requires many leased lines, and so does not scale well. Each office would require a leased line to all other offices. VPNís connecting via the Internet is a far more scalable solution, as opposed leased lines.
Through the use of link balancing and link bonding VPN's can use two or more internet connections, so if one connection at your company had a problem all VPN traffic can be sent over the remaining connections, and will automatically use the original connection when it is back up again.
Disadvantages
You have to remember though, having a VPN means having to rely on the Internet, and having to rely that your ISP (Internet Service Provider) is reliable, although this problem can be reduced by having two or more ISPís and using the 2nd in a VPN failover scenario.
Also VPNís require careful configuration, possibly some troubleshooting and the terminology can be overwhelming for administrators not familiar with the technology.
Setting up VPN with IPSec
Iíll give a quick overview in the typical way a site to site VPN is configured using IPSec. I have chosen IPSec as itís the most commonly used technology, and is known to be a solid, robust and secure VPN technology.
You may be new to all the VPN terminology, so click on the links in my VPN article to give you a good understanding on meanings within the below guide.
Basics in setting up a site to site VPN with IPSec
Below covers what is required to set up a VPN connection on a VPN gateway with IPSec. It is not really aimed at a specific vendor and is fairly general.
First you would decide how your going to authenticate both VPN peers to each other. Either select a Pre-shared key or install a digital certificate. This is used for authentication and to ensure the VPN gateways are authorised. This would prove their identities to each other. Both gateways must use the same type of credentials, so either both use Pre-shared keys or both use digital certificates. Also if you are using pre-shared keys, then both keys would have to match.
Phase 1
VPN's are configured and processed in two phases, phase 1 and 2. In phase 1 using Main mode or Aggressive mode you will set up a secure and encrypted channel, to protect your phase 2 negotiations.
1) You will need to specify both gateway addresses. So you would specify the address of the local VPN gateway, and you would also specify the address of the remote VPN gateway. You can either specify an IP address or a domain name. On some VPN gateways you could also specify an e-mail address, or if you use a digital certificate you could specify the certificates subject field.
2) Main mode or aggressive mode can be selected depending on which one you would want to use. Main mode is more secure, but slower than aggressive mode. In Main mode peers exchange identities with encryption, and Aggressive mode, although faster exchanges identities without encryption.
3) Specify whether to use Nat-Traversal. This is selected if your VPN gateway is behind a NAT device. Also specify whether you want both peers to use IKE keep-alive. This ensures that if a VPN gatewayís interface is not responding it will failover to the second interface. This is true when your ISP goes down, and your secondary interface is a backup ISP.
4 You would now decide on your transform set. This includes the type of encryption, authentication and how long your security association will last. For your authentication you can either use Sha1 or MD5. Sha1 is the stronger authentication algorithm.
For your encryption you can select either DES, 3DES or AES 128, 192, 256 bit key strength. AES is the strongest protocol.
You can specify a limit before your SA expires, which will add more security to your VPN if your keys have been hacked. Although this will also have a slight affect on performance as well.
You will need to specify a Diffie-Hellman key group, usually 1, 2, 5 or 14in which 14 is the most secure group.
You can optionally set up extra transform sets if needed. If youíre not sure on your peers transform settings, then you may want to set up more transform sets. Although it is recommended to know your peers settings and create the minimum transform setís required as it is more secure this way.
Phase 2
In phase 2 using Quick mode you would establish the IPSec SA. You would tell the gateway what traffic you will be sending over the VPN, how to encrypt and authenticate it.
1) You will need to specify what traffic will go across the VPN. So you would be specifying an IP address, Network address, or IP address range. This is access to your internal network, so either remote users from home, or the peer office can have access to resources behind the VPN gateway.
2) You can choose whether to use PFS (Perfect forward secrecy), for optional and an extra layer of security. If you will be using PFS, remember that both VPN peers must support and use PFS. You can select which Diffie-Hellman group to use for new keying material. The higher the group you select, the stronger the key.
You would now need to specify some more parameters in securing your data within the IPSec SA (Phase 2), also known as phase 2 proposals. The parameters are made up of encryption and authentication algorithms.
3) Here you first specify the type of proposal, either selecting AH or ESP. AH only provides authentication, and ESP provides authentication and encryption.
4) If you have specified ESP, which the majority would choose, then you would specify your authentication and encryption. For authentication and integrity you can select SHA1 or MD5, where SHA1 is the strongest algorithm. For encryption you can select DES, 3DES or AES 128, 192, or 256-bit key strength. AES 256 is the strongest encryption protocol.
5) You may want to specify a value for when your key would expire. This would ensure your encryption keys would change over a period of time, adding more security, as well as having a slight affect on performance. The majority leave these settings as the default. However if your a bank or any other company dealing with high confidential data then you may want to force keys to expire, and have them re-created.
Final steps
You may now need to create policies or rules to allow your VPN traffic in and out of your firewall. This may have already been done for you when you had completed configuring your gateway, and you may have had the option to either enable or disable your VPN gateway to automatically doing this for you, all depending on the product functionality.
You can now save all changes to your VPN gateway.
You are done in configuring your VPN gateway, and you can now configure the peer VPN gateway. Remember to configure your peer VPN gateway with the exact same settings as you configured your local gateway, or else the VPN tunnel will not form successfully.
Final words
The above article I have wrote is not specific to any VPN gateways, so you may find differences in order of settings or slight difference in terminology used, although I come from a Watchguard, Fortinet, SonicWALL and Cisco background and so you may find my instructions to be very like how you would set up those firewall VPNís. However configuring VPN with IPSec is a standard set of parameters and settings, and the major differences you would see would lie within the GUI, and possibly some slight naming alterations.
In a nutshell, with all VPN gateways using IPSec, you would have to configure your VPN gateway addresses, phase 1 settings, phase 2 settings, adjust firewall policies and save the configurations, in which ever vendor product you work with.