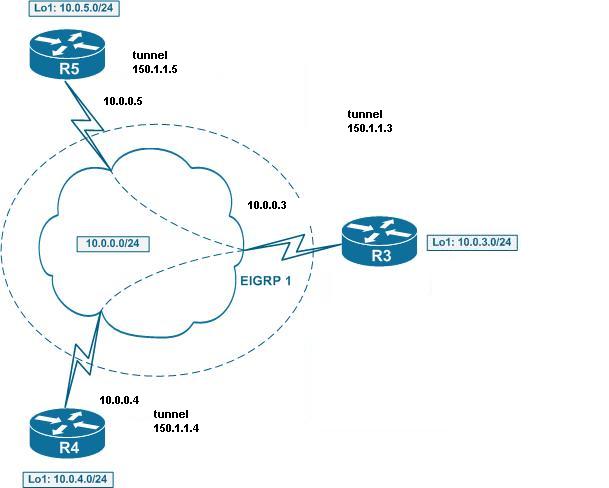
R3 Configuration
#crypto isakmp policy 10
encr 3des
Hash md5
authen pre-share
#crypto iskmp key CISCO address 0.0.0.0 0.0.0.0
#crypto ipsec transform-set NETSET esp-3des esp-md5-hmac
#crypto ipsec profile NETPROFILE
set transform-set NETSET
#int tunnel 0
ip add 15.1.1.3 255.255.255.0
tunnel source F0/0
tunnel mode gre mulipoint
tunnel key 123
ip nhrp network-id 123
ip nhrp authentication CISCO
ip nhrp map multicast dynamic
tunnel protection ipsec profile NETPROFILE
R4 Configuration
#crpto isakmp policy 10
encr 3des
hash md5
auth pre-share
#crypto iskmp key CISCO address 0.0.0.0 0.0.0.0
#crypto ipsec transform-set NETSET esp-3des esp-md5-hmac
#crpto ipsec profile NETPROFILE
set transform-set NETSET
#int tunnel 0
ip address 150.1.1.4 255.255.255.0
tunne source f0/0
tunnel mode gre multipoint
tunnel key cisco
ip nhrp networl-id 123
ip nhrp authentication CISCO
ip nhrp map 150.1.1.3 10.0.0.3
ip nhrp map multicat 10.0.0.3
ip nhrp nhs 150.1.1.3
tunnel protection ipsec profile NETPROFILE
R5 Configuration
#crpto isakmp policy 10
encr 3des
hash md5
auth pre-share
#crypto iskmp key CISCO address 0.0.0.0 0.0.0.0
#crypto ipsec transform-set NETSET esp-3des esp-md5-hmac
#crpto ipsec profile NETPROFILE
set transform-set NETSET
#int tunnel 0
ip address 150.1.1.5 255.255.255.0
tunne source f0/0
tunnel mode gre multipoint
tunnel key cisco
ip nhrp networl-id 123
ip nhrp authentication CISCO
ip nhrp map 150.1.1.3 10.0.0.3
ip nhrp map multicat 10.0.0.3
ip nhrp nhs 150.1.1.3
tunnel protection ipsec profile NETPROFILE